

King Fahd University of Petroleum & Minerals
Information and Computer Science Department
ICS 444: Computer and
Network Security (3-0-3) [Elective Course]
Syllabus – Spring Semester 2014-2015 (142)

Website:
All
course material and resources are posted in Blackboard (WebCT)
http://webcourses.kfupm.edu.sa
Class Time, Venue and Instructor Information:
|
Time |
Venue |
Instructor |
Office Hours |
|
UTR
10:00-10:50am |
23/014 changed to 24/141 |
Dr. EL-SAYED EL-ALFY
Office: 22-108
Phone: 03-860-1930
E-mail:
alfy@kfupm.edu.sa,
http:faculty.kfupm.edu.sa/ics/alfy
|
Announced on Blackboard |
Course Catalog Description
Pre-requisites:
Course Objectives
![]() Develop a fundamental understanding of computer and network security proper
practices, policies, technologies and standards.
Develop a fundamental understanding of computer and network security proper
practices, policies, technologies and standards.
Course Learning Outcomes
Upon completion of the course, you should be able to:
Required Material
![]() Lecture Handouts
Lecture Handouts
Other Recommended References
Assessment Plan
Tentative Schedule
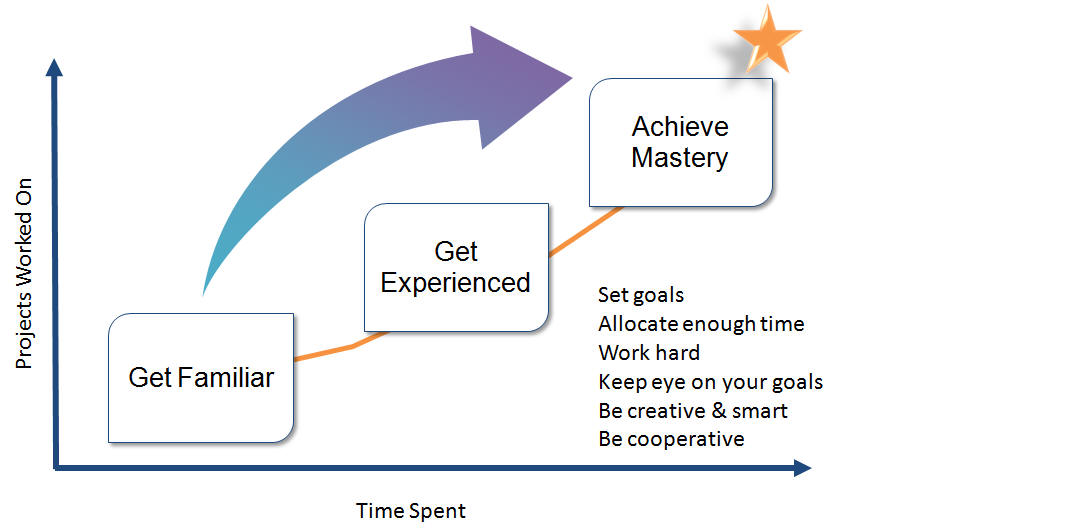
How to do well and become a star?
Other Resources on the Web: