

King Fahd University of Petroleum & Minerals
Information and Computer Science Department
SEC 511: Principles
of Information Assurance & Security (3-0-3)
[Graduate Course]
Syllabus – Fall Semester 2015-2016 (151)

Website:
All
course material and resources are posted in Blackboard (WebCT)
http://webcourses.kfupm.edu.sa
Class Time, Venue and Instructor Information:
|
Time |
Venue |
Instructor |
Office Hours |
|
MW 20:00-21:15 |
24-104 |
Dr. EL-SAYED EL-ALFY
Office: 22-108
Phone: 03-860-1930
E-mail:
alfy@kfupm.edu.sa,
http:faculty.kfupm.edu.sa/ics/alfy
|
Announced on Blackboard |
Course Catalog Description
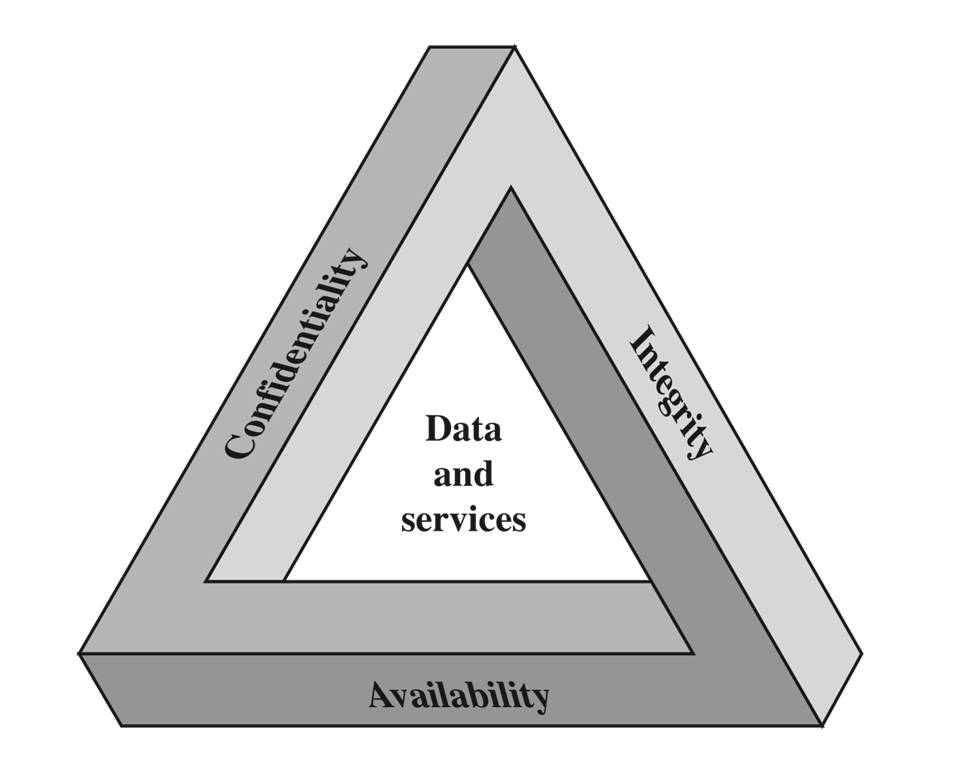
Introduction to information assurance and security. Information confidentiality, availability, and integrity. Security systems lifecycle. Risks, attacks, and the need for security. Legal, ethical, and professional issues in information security. Risk management including identification and assessment. Security technologies and tools. Security laws, audit and control. Cryptography foundations, algorithms and applications. Physical security, security and personnel, security implementation and management. Securing critical infrastructure. Trust and security in collaborative environments.
Pre-requisites:
Course Objectives
![]() This course is an introductory course to information assurance and security
(IAS). It provides a wide coverage of a variety of technical and administrative
aspects of IAS.
This course is an introductory course to information assurance and security
(IAS). It provides a wide coverage of a variety of technical and administrative
aspects of IAS.
Course Learning Outcomes
Upon completion of the course, you should be able to:
Required Material
}
No
official textbook for the course. However, a number of selected book chapters
and papers will be identified throughout the semester.
}
Lecture notes and some recommended websites
}
Other Recommended References
}
Principles of Information Security, 5/E, Michael E. Whitman, Herbert J.
Mattord, Cengage Learning, January 2014.
}
Computer and
Information Security Handbook, John R. Vacca (Ed.), MK, Elsevier, 2013.
[Available thr
sciencedirect.com]
}
Cryptography & Network Security, Behrouz Forouzan, McGraw-Hill, 2008.
}
Cryptography and Network Security: Principles and Practice, 6/E,
William Stallings,
Prentice Hall, 2014.
}
Security+ Guide to Network Security Fundamentals, 5/E, Mark Ciampa, Course
Technology, 2014.
}
Hacking
Exposed: Network Security Secrets and Solutions, 7/E, Stuart McClure, Joel
Scambray, George Kurtz, McGraw-Hill Osborne, 2012.
}
Hacking
Exposed Malware and Rootkits, Michael Davis, Sean Bodmer, Aaron LeMasters,
McGraw-Hill Osborne, 2009.
}
Hacking
Exposed Web Applications, 3/E, Joel Scambray, Vincent Liu, Caleb Sima,
McGraw-Hill Osborne, 2010.
}
Computer Viruses
and Malware, John Aycock, Advances in Information Security, Springer, 2006.
Assessment Plan
Assessment
Tool
Weight
Coursework:
Blogs, Assignments, Presentations & Quizzes
15 %
Term Project
30 %
Midterm Exam (9th
week on Wednesday, Nov. 17)
25 %
Final Exam
(semi-comprehensive) [As announced by the registrar: Dec. 17@7PM]
30 %
Tentative Topics and Some References
}
Research skills: Writing academic
papers, Latex, GNUPlot. (Plenty of online resources)
}
Introduction to Information Assurance
and Security (Ch. 1, Principles of Information Security)
}
Overview of Cryptography (Selected
chapters from Cryptography and Network Security Book).
}
Securing Organizations (Ch.1, Security
Handbook)
}
System Intrusions (Ch. 3, 4, Security
Handbook)
}
Firewalls (Ch. 21, Security Handbook)
}
Mathematical Model to Security Policies
}
Malware (Ch. 2,3, Computer Virus and
Malware Book)
}
Web Application Security (OWASP
Resources)
}
Computer and Network Forensics (Ch. 19,
20, Security Handbook)
}
Trust and security in collaborative
environments
}
Legal, Ethical, and Professional Issues
(Ch. 3, Principles of Information Security, Saudi Laws).
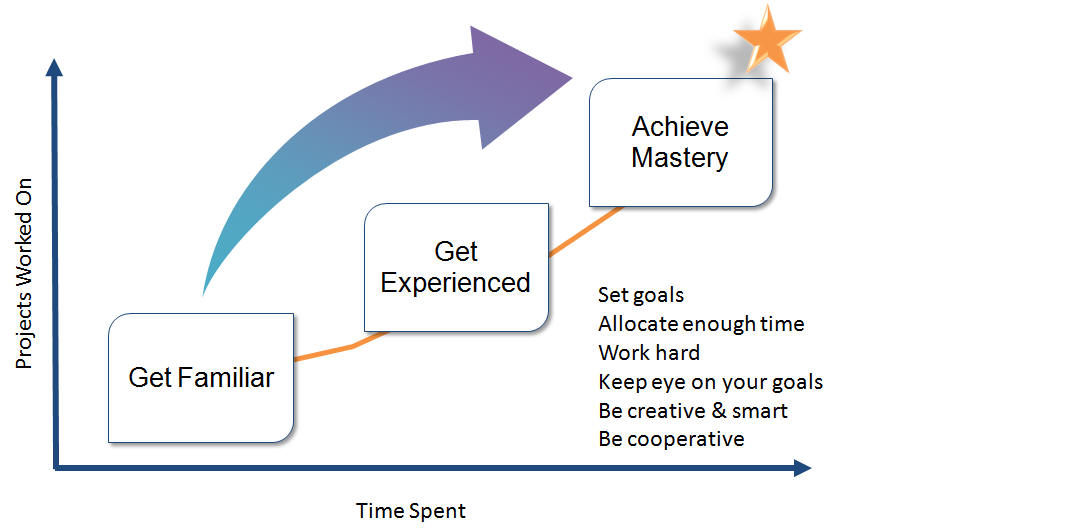
How to do well and become a star?
Academic Skills
} How to write a good research paper and give a good research talk
} How to Give an Academic Talk, PDF
} Paper Writing and Paper Reviewing
} A simple guide to LaTeX - Step by Step
} ShareLaTeX, the Online LaTeX Editor (Documentation)
Other Resources on the Web:
} NIST Glossary of Key Information Security Terms
} SANS Information Security Training - Cyber Certifications - Research
} SANS Institute: Information Security Resources
} SANS Institute- Reading Room
} OWASP
} CISSP - Certified Information Systems Security Professional
} Information Security Training Boot Camps - InfoSec Institute
} Black Hat - Featured Video Archive
} Bishop Computer Security Textbooks
} SecTools.Org Top Network Security Tools
} Secure Coding - The CERT Division
} Microsoft Internet Safety and Security Center
} USENIX
}} Some Related Courses at Other Institutions